Customers put their ultimate trust into service providers whether they know it or not. Test reports contain an extraordinary amount of sensitive data and with the right combination of knowledge and tools, an adversary can piece together the details of an entire distribution system and how its protected.
High profile clients and government entities need to keep their data secure, however, the standard solution for many small testing agencies is to send unencrypted data across the open internet to be stored in unsecured SQL databases.
Source information is usually stored in an unencrypted, password protected hard drive and distributed among all technicians in the company, presenting a huge data breach risk. The data is also entirely controlled by the testing company, not the client.
The theft of a laptop or database file can be detrimental to a service company and the clients they serve. Fortunately, there are several easy steps that can be taken to help minimize this risk and better protect your customers.
Personnel Risk and Centralized Control
The solutions at this level are two-fold because we need to think about personnel in addition to hardware. When your biggest risk of data breach comes from the human element, does it make sense to give a new team member full access to the data vault?
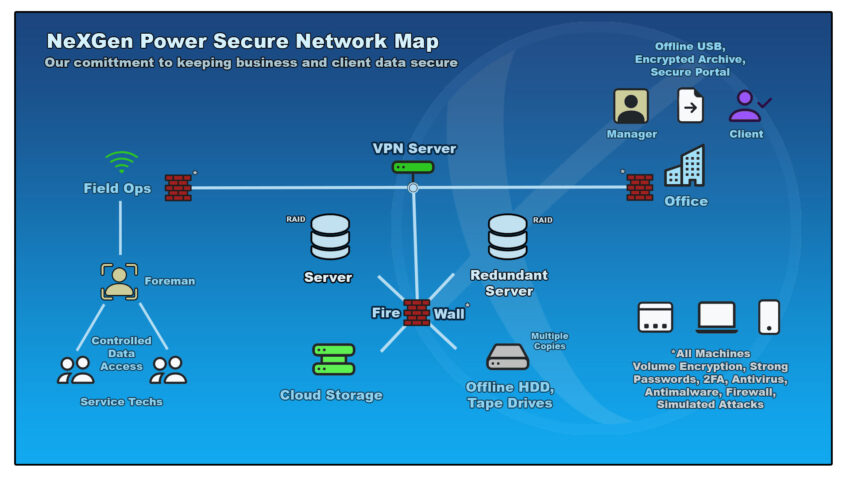
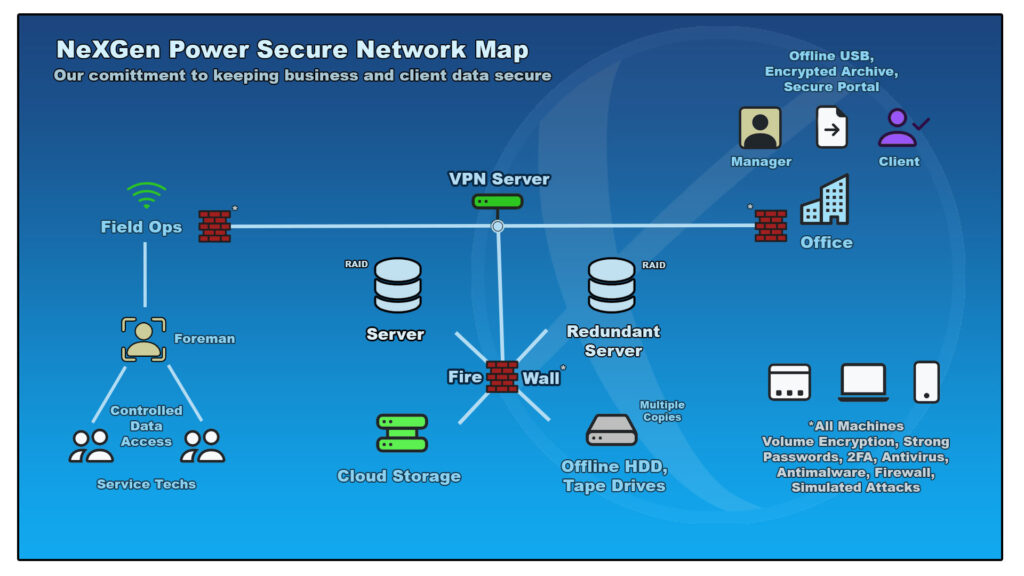
Obviously the highest risk of data breach comes from the field service arm of your organization. Many testing companies utilize SQL based test management software which synchronizes test data from a central database to each field laptop.
There is no getting around the need to share test data among technicians. In today’s fast pace service environment, its possible for a project to change hands many times. When performing yearly maintenance, historical data is a must have in the field in order to determine whether a problem is getting worse or improving but this convenience comes at a cost in terms of data security.
Managers need to take into consideration compartmentalizing test data by only allowing it to be controlled by trusted and tenured employees. Instead of giving everyone on the job a laptop with full file access, have the crew fill out paper sheets while a trusted person enters everything into a database and turns the paper back into the office.
Same goes for historical data, the job foreman should have a hard copy of prior test reports that can be dispersed to the crew and returned at the end of the job. Managers receive all of the data back directly from the job foreman rather than each crew member individually.
Leadership might find that while this approach is not as convenient as direct electronic entry from each participant, it offers greater accountability from the top down, especially between the foreman and technicians performing the work. Make sure the software suite you invest with features a robust permissions system that allows you to control what your employees can or cannot see.
Another way to compartmentalize data when using SQL based software would be keeping individual files for each project in the field that are later synchronized to a central database containing all client data. This allows for technicians to enter data electronically without allowing them full access to projects they may not be associated with.
Employees should also be required to fill out a non-disclosure agreement in regards to the information they are exposed to about test data and their clients power systems. Managers need to consider if a technician was to go to a competitor, they have access to a wealth of information that can easily be duplicated.
Hardware and Software Risks
Contrary to popular belief, a password does very little to protect a file from brute force attack. Without encryption, its possible to remove a hard drive and browse the contents from another machine.
Encryption secures the raw data on your hard drive by storing it as scrambling contents so it cant be read without a recovery key. Most businesses operate on a Windows environment, and for that reason software like BitLocker can help you create a secure environment like this for your data.
BitLocker differs from most other encryption programs because it uses your Windows login to secure your data, meaning no additional passwords are needed. Once you’re logged in to your PC, the files look just like they would otherwise and everything gets secured again once you log out.
If someone was to gain access to the encrypted drive, all they would find is unreadable data unless they knew the secret key. This protects from random attacks but not those from within your organization. What’s the policy if a technician “loses” their laptop?
Having everyone in the company regularly change their password is another great way to help keep things secure. Maintain a strict policy on their strength and often they must be changed.
Two-Factor Authentication is a highly recommended security method where you need two forms of “identification” to unlock an account. The first factor is typically a password and the second can be in the form of a code sent via email, text, or by third party application on a separate device.
The problem with two-factor is that it can become very hard to recover your account in the event you lose access to the second device, such as if you lost your phone or access to an email account when you need it most.
Data Transfer Risks
We live in a world where information can literally be snatched out of the air thanks to public WiFi and personal hot spots When you’re answering customer emails on your lunch break or submitting project files at the airport before you get on a flight, someone may be tracking your online activity.
Even when using home network, data is vulnerable. Using a Virtual Private Network will protect your data by adding an additional encryption layer when your data is transmitted over the internet. VPN’s are kind of like BitLocker for your internet connection and can be installed on just about any device with an internet connection
There is very little reason why a company shouldn’t use one to protect customer test data. Just like with online storage, companies have the option of using an existing VPN service or operating their own VPN server.
Phishing and Malware Risks
This one is pretty obvious because just about everyone should be aware by now that browsing sketchy sites can lead to trouble and you should have security software installed. All it takes is one click for your private information to land in the hands of an internet stranger.
Its important to monitor what your employees are doing on company hardware but equally important to provide adequate and persistent training when it comes to how to identify these types of attacks. You can also test your team by sending out intentional simulated phishing attacks and then re-train those who fall for the trap.
Risk of Data Loss
Periodic backup of your data is also critical in the event of hardware failure or other unexpected event that can result in permanent loss. Encryption needs to be taken into consideration at this level as well.
Redundancy and RAID arrays are a must at the server level and offline backups should be performed once a week at minimum. If using an online backup service, keep a VPN in mind and perform your due diligence when it comes to choosing a service with the best security.
External Hard Drives and Tape Storage are the final destination for data that needs to be archived, perform these backups as often as you can and maintain multiple sets. You will want to make sure this data is encrypted and stored in a locked vault with the proper air temperature and humidity.
The Perpetual Game of Cat and Mouse
Most of the topics discussed here are fairly standard IT practices that should be implemented just about any test company but keep in mind there is more to every story and new methods are being created every day in an attempt to access your data.
You can rest assured that we implement these strategies and more at ARAiUM to keep our business and client data safe. Our experts can help you also implement these processes and tailor a system to suit your companies specific needs and budget.